To review, the 3 factors of authentication are referred to as: something you know, something you have and something you are. Today, in part 3 of this series, we'll talk about the failure of the second factor of authentication, "something you have". Here are links to parts 1 and 2 of the series.
While not the oldest form of authentication, this factor of authentication has been around for a long time. Think about a key, or perhaps some kind of scroll with the symbol from a leader, or even the sword in the stone! A driver's license, ID card, credit card or passport is also something you have. These are all things someone can have and can be used identify them or grant access.
Today, the term "2-factor authentication" can the use of any two different factors of authentication. But most commonly it refers to the combination of password or PIN that you know, with a single use 6-digit number from some kind of token.
Here are the three most common single use string/token delivery methods:

Hard Token. Also called a fob. This can be a small oval, rectangular, card-shaped or key-shaped plastic, battery operated device with an led screen. They typically display a 6-digit number. These numbers can either be calculated using a time-based or sequence-based algorithm. Time-based means the value displayed is calculated based on synchronization with time clock on the server. Sequence-based means values are displayed in a predetermined order. An example of a hard token is the paypal "football" token or the Yubikey.
 Smart cards and key cards are special cases of hard tokens. In addition to, or instead of, the one-time numerical string, smart cards can have a chip or a magnetic strip that can hold additional information. Use of a smart card for 2-factor authentication is sometimes called "chip and pin" authentication.
Smart cards and key cards are special cases of hard tokens. In addition to, or instead of, the one-time numerical string, smart cards can have a chip or a magnetic strip that can hold additional information. Use of a smart card for 2-factor authentication is sometimes called "chip and pin" authentication.Smart cards do scare me a bit because they can hold a lot of additional information that can easily be stolen.
Key cards are typically ID cards with an RFID chip used with a card reader to get physical access to a locked area in a building.
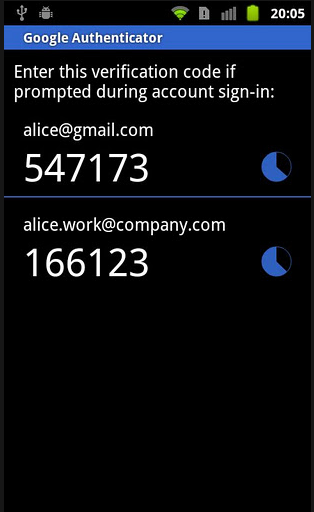
Soft Token. A soft token is simply a program or app you can run on a computer, tablet, smartphone or other device that provides the single-use numerical string similar to that delivered by a hard token. The advantage of a soft token is that you can have your 2nd authentication factor on a device you already own and carry rather than having yet another token. And one device can run multiple soft tokens. A great example of a soft token is Google Authenticator.
SMS delivery. A single-use authentication string can also be delivered via text message to a smart phone or feature phone. These are generated the same ways as listed above.
Paper. As a bonus 4th method, some authentication methods can generate a set of single use or challenge-response strings that are printed on paper and carried. Examples include one time passwords in LastPass and Steve Gibson's Perfect Paper Passwords. Even though these are passwords, they are designed to be possessed and read/typed from the paper you have rather then memorized or known. This method is less commonly used.
Well, we're talking about the failures of these authentication methods. The 2nd factor, something you have, very quickly degenerates into something you lost. Perhaps the most common support issue with hard tokens is that they get lost. Though a bigger issue is that users often keep them right in their laptop case, with their laptop, essentially rendering any strength they add to the authentication process useless.
And if one has to authenticate to systems on different networks, you may need to have something for each of these networks! More items to lose!
As mentioned above, authentication string delivery via a soft token has the advantage of using a device the user already owns and usually carries. And multiple tokens can run in the same device. Another advantage is that people never lose their phones. Or break them. And key card readers can't be hacked...
Oh wait...
Despite some major deficiencies, tokens hold some promise, primarily as a delivery device for single use or one-time passwords (OTP).
Can you think of other examples of "something you have" devices? How do you use the second factor of authentication? Do you have any great stories of how tokens were lost and/or misused?
No comments:
Post a Comment