Last week the excellent tech new site, Ars Technica, did a feature article in which they had first a journalist, then three different password hacking experts, try to decrypt passwords from an encrypted password file. They were all quite successful... frighteningly so.
Steve Gibson discussed this for a bit in Security Now episode 406.
But, I think there were some critical flaws in the test. And there were also some excellent lessons.
I'll comment on the article using the sandwich method, starting with what was good...
First, I think the article did a nice job of digging into the techniques used to crack passwords. All the participants started with the same freely-available tool, oclHashcat-plus. How they chose to use brute-force methods and, in particular, how they cultivated and used their dictionaries, is where the art comes in.
Classic brute-forcing involves either:
- testing a bunch of dictionary words or oft-used passwords against the encrypted pw file, or;
- trying every character-combination for a given character set and password length.
 "a brute-force crack for all passwords containing one to six characters,
meaning his computer tried every possible combination starting with "a"
and ending with "//////." Because guesses have a maximum length of six
and are comprised of 95 characters—that's 26 lower-case letters, 26
upper-case letters, 10 digits, and 33 6 + 955 + 954 + 953 + 952 + 95."
"a brute-force crack for all passwords containing one to six characters,
meaning his computer tried every possible combination starting with "a"
and ending with "//////." Because guesses have a maximum length of six
and are comprised of 95 characters—that's 26 lower-case letters, 26
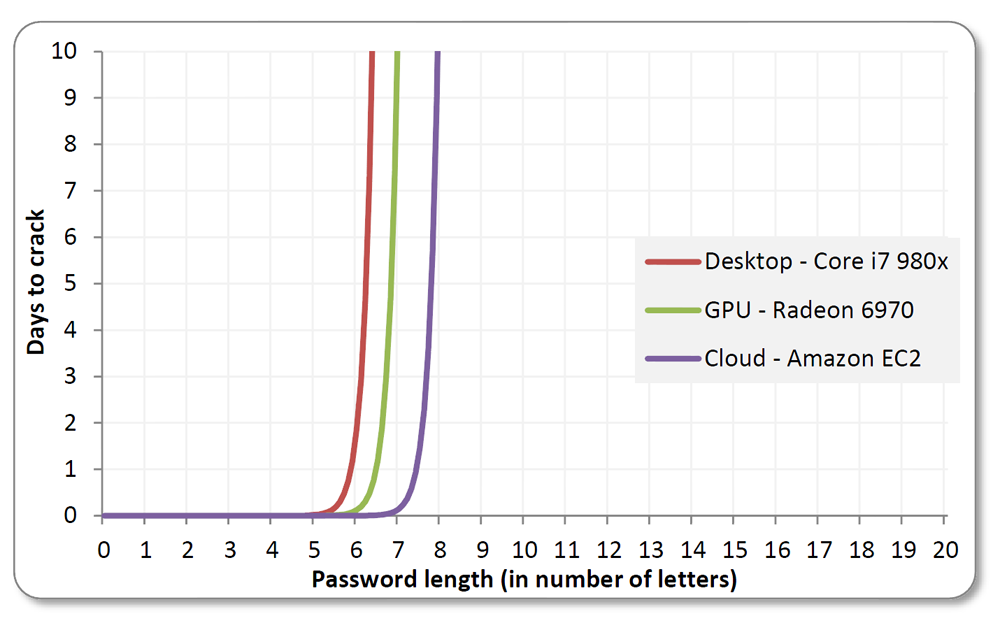
upper-case letters, 10 digits, and 33 6 + 955 + 954 + 953 + 952 + 95." Clearly the difficulty of the brute-force attack increases with password length.
So here is where the art comes in... experienced crackers know that people often create "complex" passwords using dictionary words "roots" connected by numbers or special characters. Many classic "complex" passwords look like this. This is the important point... they can have the cracking tool focus on passwords of that form! So don't choose passwords like that!
Now for the bad... the cracking was done on an a poorly encrypted password file. First, they used MD5. That hash is known to be weak with problems first discovered in 1996!
Next, the hash was applied without salt. Salting ads random characters to the password before being hashed. This would have helped defeat a "rainbow table" attack (old school), but also slows down brute force computational attacks.
Finally, this password file used just a single pass through the hash function. Multiple iterations makes the attacks used far more computationally intensive, making it take longer.
So, while the experts ripped through this password file, it did use very weak encryption. But we have no control over the encryption used at online sites. And some sites do use weak encryption (and/or don't protect their password file).
Now back to the good advice. And this is the most important point for people who have passwords to online sites. We see that most passwords that people might choose can be cracked. And that long passwords are hard to crack (but hard to remember).
The caption of this xkcd comic says it all: "through 20 years of effort, we've successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess."
This means we need to use:
- long passwords (Steve Gibson's password haystack process is a way to add length)
- random passwords
What other password creation tips and ideas do you have?

No comments:
Post a Comment